SVreX
MegaDork
4/3/16 5:57 p.m.
Pretty sure my 83 yo Mom has been scammed. She had an experience this week that pretty much exactly mirrored those described in these articles:
Computerworld article
Malwarebytes article
Computer locked up, popup told her she was infected and needed to call tech support, she called (allegedly Apple), gave remote access to him, "Apple tech" eventually said she needed to hire another company, who eventually "fixed" the problem and charged her $500.
They spent 7 hrs with remote access to her computer, going through everything. Passwords, accounts numbers, all kinds of stuff. Oh yeah- Indian accents for everyone.
Anyway, there is a part I can't figure out...
She paid by check, and mailed it. She mailed it to a company that appears to be legit, but they don't do tech support for Apple. The company's name is ITech Global 3248 Sutton Ct Fremont, CA.
How would a scammer intercept a check payable to a real company and then cash it in another country?
Or have these scammers just put a lot of effort into appearing to be "real"?
Teach me...
I'd think stopping payment on the check would be the first thing...?

Mike
Dork
4/3/16 6:04 p.m.
I would suggest getting law enforcement involved really soon. This check means someone connected to the scam, even if only a money mule, has to physically handle the check.
Not that this means too much, but that address is someone's house.

SVreX
MegaDork
4/3/16 6:13 p.m.
slowride wrote:
Not that this means too much, but that address is someone's house.
Yeah, just figured that out. They've even got a pretty nice website. 

SVreX
MegaDork
4/3/16 6:17 p.m.
...and they've bought their way to a pretty high Google search.
Yeah, I've seen real corporate websites that were worse. Although I have noticed that scammer corp sites always put the logos for Facebook, Twitter, and LinkedIn, but they never link them to anything. Which makes me think it's probably a template or something easy to cut and paste.

SVreX
MegaDork
4/18/16 8:29 p.m.
OK, so the follow up to this story...
Somewhere in the whole mess, she signed a contract she thought was for "computer security protection"- to protect her form any malware (like what they installed). Of course, she didn't read the contract. Turns out, it was a contract that basically waived their liability, and made it her fault for anything they did (like her sharing information with anyone who calls from their company). It also authorized bank transfers. Sneaky bastards actually conned an old woman into signing a contract that gave them legal permission to steal from her, and made it her fault (because they warned her not to do it). They are pretty good at what they do.
We locked down everything. Changed all the credit cards, reported identity theft to the Police, the IRS, the banks, the financial manager. Cancelled the transfer authorizations. Cancelled the check. Changed all her passwords, and even her IP address. Added PIN to her IRS account. Looks like she had no actual loss, except for the PITA factor.
Today she gets a phone call from a local area code. Guess who?
Same voice, just calling to "check up on how things are going". Azzhats picked up a prepaid phone (probably in India), and had an available number with a local area code assigned to it. Scared her pretty bad (she thinks they are nearby, looking to cause her bodily harm. I explained to her that a good IT person can make a phone behave like that from the other side of the world. These jokers are probably not even in this country).
I don't think they realize yet how much we locked down. They found a sucker. They intend to milk it for all they can. Any little bit she gives them they will try to use to steal from her.
Watch out. The world has some real azzhats in it. And older people are really easy targets.
In reply to SVreX:
Did you wipe the computer or quarantine it? If they installed a backdoor while they were in there... they can reconnect to it anytime it connects to the internet. The bad news is that they can do that - the good news is that if they do and are even a tiny bit careless... you can find them. Your local FBI agent will know how ;)

SVreX
MegaDork
4/18/16 8:53 p.m.
In reply to Huckleberry:
Would they be able to do that with a new IP address? (I think I know your answer)
LE suggested we change the IP address, but didn't mention anything about wiping or quarantining.
In reply to SVreX:
Yes, because the infected device reaches out to the mothership. I'm not saying that is the case here either - but it's easier to wipe it and start fresh than to explain how to port block/sniff.
Although being that it's an OS-X machine you can install an application firewall that is reasonably effective. Google an application called "Little Snitch". It will log attempts and offer allow/block for any executable trying to use the network. Block anything you don't recognize as reasonable and investigate the calling program. You can also do this with your router at the network level if she has one. It's a good idea anyway if she does not because a compromised machine can lie to application firewalls if the problem is sophisticated enough. It can't manipulate peers though (well... not without being seriously cool, anyway).
Sorry to hear about your troubles. I had a call from Jamacia the other day.
Scammer: " hello sir we are calling from publishers clearning house"
Me: "wow"
Scammer: "We sent you a letter the other day did you get it"
Me: "No"
Scammer: "Do you still live in north carolina"
Me: "No"
Scammer: " Ohh I mean South Carolina, do you still live there"
Me: " no"
Scammer: " are you interested in winning the publishers clearing house?"
Me: "No"
Scammer: Click!
Wait.. I thought Apple products were immune to anything malicious?
Similar happened to my father-in-law with a Windows machine. Like you, I'm not quite sure what to make of it. Because it sorta appears to be legit.
Don't remember exactly how it started, but it was similar to your mother. Ended with him paying several hundred dollars and someone with an Indian accent spending hours on his machine via remote access. In the end, they did fix all the problems he was having.
Even weirder, they gave him several years of follow up service, and have provided it to him.

SVreX
MegaDork
4/19/16 6:16 a.m.
In reply to foxtrapper:
The scam is that the "problems" they "fix" were created by them.
Google "Tech support scam".
Basically, they generally create a pop up window that looks scary and official, claiming serious system failure, and giving a tech support phone number. When you call, you give them remote access to your computer. Then, they run a script which looks like they are doing significant work (and that your computer is seriously messed up), while they access stuff in the background.
The amazing twist is that they even provide a contract whic would make their actions legal in court.
Read your Dad's service agreement for the service they provided. I guarantee its twisted. I'll bet it auto renews too, doesn't it?
novaderrik wrote:
Wait.. I thought Apple products were immune to anything malicious?
They don't pick up spyware and viruses passively like Windows systems, but if you go ahead and give somebody access to the system at an administrative level (basically compromising the security of the system) all kinds of bad things can happen. A bank vault isn't very secure if you give a set of keys to the robbers...
I get those messages occasionally . I just shut down the computer and it goes away.
pointofdeparture wrote:
novaderrik wrote:
Wait.. I thought Apple products were immune to anything malicious?
They don't pick up spyware and viruses passively like Windows systems
Do windows systems still pick up that stuff passively? The last one I can remember was conficker back in 2008.
Also:
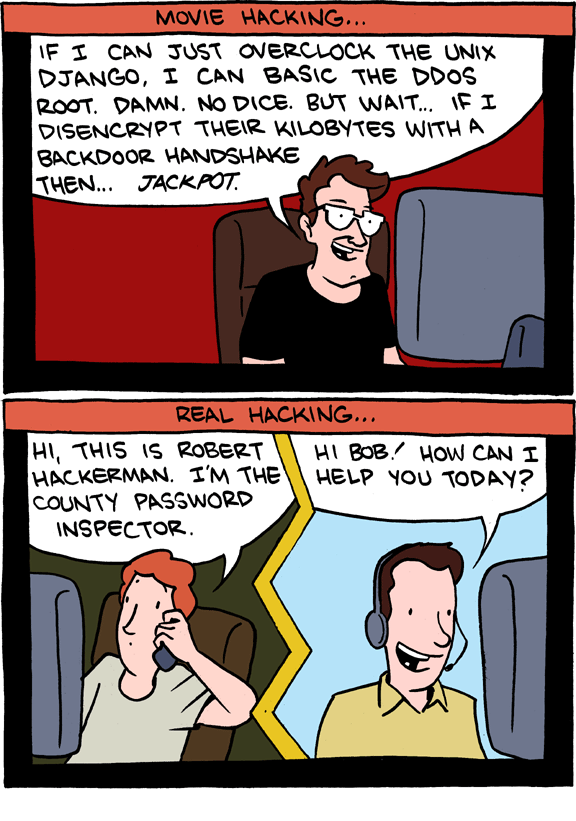
SVreX wrote:
In reply to foxtrapper:
The scam is that the "problems" they "fix" were created by them.
I do understand that. But, it didn't quite go down that way. Don't remember the hows and wherefores of the event, and he's a sharp tool when it comes to business.
As I recall, he even contacted Microsoft directly and they told him it was a legit service they provide through sub-contracting or such.
Like I said, at first I thought he'd tangled with a hustle/scam, but the more I watched and learned of it, the less sure of it I was.

SVreX
MegaDork
4/19/16 9:37 a.m.
In reply to MCarp22:
That summarizes it pretty accurately.
Damn, just saw this thread...the contract thing is a nasty new twist. I'd airgap that computer real quick, at least give it a very thorough virus scanning, or maybe even wipe it if that's practical...if not, after a thorough scanning I'd monitor network traffic when reconnecting it. Make sure the passwords they have are changed to very strong passwords, because they already have the username. I'd even abandon any of those accounts where the credentials were stolen if practical.
We really need to get the word out that if you receive an email or any kind of notification to call a phone number on your computer, DON'T DO IT.

SVreX
MegaDork
4/19/16 10:34 a.m.
In reply to GameboyRMH:
Yeah, I'm gonna try to post the content of that contract in a day or so.
I read it and said, "Mom, are you crazy?" Of course, she admitted she never read it before signing it. I showed it to the LEO, and he agreed that it would likely make them innocent, because she had signed a contract allowing them to do everything they did (or specifying that she should NOT allow any of their employees to do most of what they did).
My dad got hit by one of those fake spy ware removal companies a while ago.. He had to wipe his computer to get it to go away.